message-level security
master course
Lecture details: https://informatik.rub.de/studium/lehrveranstaltungen/mls/
This lecture focuses on Message-Level Security and explores different methods such as JSON, REST, OAuth, OpenID Connect, SAML, and PDF, highlighting common errors and attacks. The lecture is inspired by my current research and offers practical exercises using the eHacking virtual machine, making it an essential topic for anyone interested in cybersecurity.
The Faculty of Computer Science awarded this lecture with the Excellent Teaching Award.
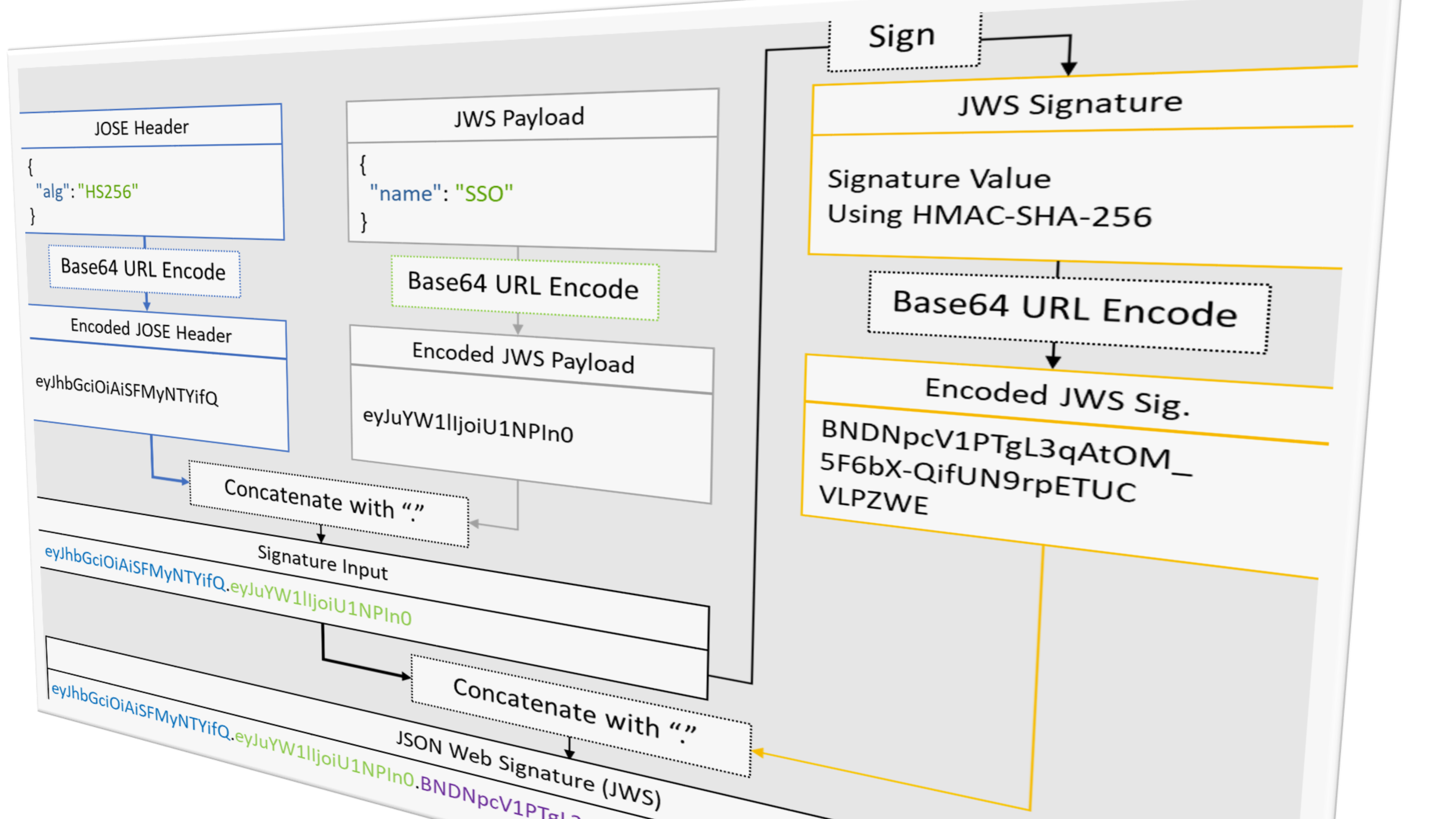
The lecture covers the topic of Message-Level Security. Unlike SSL/TLS, which establishes a secure transport channel, message-level security is about protecting messages - such as HTTP requests - at the message level. The correct use of cryptographic methods as well as a secure provision of API interfaces are important here.
In the course of this lecture, different methods of message-level security will be discussed. The lecture deals with different methods of message-level security:
- JSON is a universal data description language that is supported by every modern browser, among others. With the help of JSON Signature and JSON Encryption JSON messages can be protected directly. But is this enough or can these security mechanisms be bypassed?
- REST is a paradigm for sharing ressources using APIs. What can go wrong when using these APIs? What are the most common security flaws?
- OAuth is a very widely used technology for delegating permissions and is nowadays used by all major websites like Facebook, Google, Twitter, Github, and many more. The lecture explains in-depth details and common errors/attacks that can occur when using OAuth.
- OpenID Connect is an extension for OAuth to authenticate users on websites using a third party (single sign-on, e.g. Google Login). OpenID Connect has become the defacto standard for third-party web logins in recent years. The lecture will explain in detail what the differences are to OAuth and which attacks are possible on OpenID Connect.
- SAML stands for Security Assertion Markup Language and is a single sign-on standard that is becoming more widely used in business scenarios. However, numerous attacks exist from identity theft to remote code execution.
- PDF is probably the most widely used universal document exchange format. In this lecture, the security properties of PDFs will be examined. In particular, digital signatures will be examined, which are used, for example, for contracts. Will we be able to forge signed documents?
Students will be given an in-depth understanding of the systems. Attacks are presented for all systems studied, from both academia and the pentesting community. The exercises offer the possibility to try out the learned knowledge practically. For this purpose, students are provided with a virtual machine. This eHacking virtual machine won the 5x5000 Competition: ‘Online or presence teaching - it fits!’.
This lecture is heavily inspired by current research. It includes and discusses recently published research papers in this area.